Securing the Web Application Content
SEI can be embedded into other websites. This is required for some Sage products such as Sage 300, which integrates SEI within its own websites.
However, this enables the possibility of a hostile entity to embed SEI into a malicious site and allows for clickjacking.
To prevent this, you can add a Content Security Policy called frame-ancestors that will allow only the specified websites to embed SEI.
There are two ways to add the Content Security Policy.
To add the Content Security Policy using the web.config file:
-
Open File Explorer and navigate to C:\Program Files\Sage\SEI Server\WebServer\Web.config.
-
Locate the customHeaders tag.
-
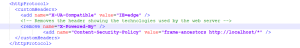
Add this line:
<add name="Content-Security-Policy" value="frame-ancestors http://website1.url.com https://website2.url.com />
Examples of websites URLs:
http://example.nectari.com
https://*.nectari.com
For further examples, refer to CSP: frame-ancestors.
-
Save the file.
To add the Content Security Policy using IIS:
-
Open IIS Manager:
-
Press the Windows key + R to open the Run window.
-
Type inetmgr and press the Enter key.
-
-
Under the IIS section, open HTTP Response Headers.
-
In the Actions panel on the right, click Add.
-
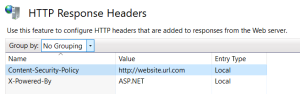
In the Name field, enter Content-Security-Policy.
-
In the Value field, enter the website URL.
-
Click OK.
-
Repeat steps 3 to 6 for each website you wish to add.
X-Frame-Options
x-frame-options is the former way of securing the SEI application. The ALLOWFROM directive would be the recommended way to specify which website(s) can embed SEI. For further details about supported browsers, refer to Browser Compatibility.
The ALLOWURL directive is OBSOLETE and no longer works in most common browsers (including Chrome and Firefox). It should NOT be used.
Also, the SAMEORIGIN and DENY directives still work correctly but they are not the recommended way to secure SEI.