Role Configuration Guidelines
Use these guidelines to configure roles in a way that ensures appropriate access to features, protects sensitive data, and supports your organization’s governance model.
This topic builds on the general role setup described in the Roles topic by offering best practices for assigning permissions to the predefined SECURITY and BASIC roles.
General Guidelines
-
Understand the default roles: Before assigning permissions, it's important to to understand the purpose of each predefined role:
-
SECURITY
Intended for administrators or super-users who manage data models, OLAP cubes, governance rules, distribution jobs, and environment configurations. -
BASIC
Designed for users who use existing reports, dashboards, and views, and may create their own versions. This role should not have permissions that allow system-wide changes.
-
-
Assign only the required permissions: Grant only the permissions needed for the person to complete their tasks.
-
SECURITY
Select all permissions required for full platform access, including creating, modifying, and deleting data models, views, and procedures. -
BASIC
Assign permissions that allow interaction with content, such as viewing and creating dashboards or reports. Avoid permissions that affect data models or system-level configurations.
TipAssign each role to a test account and verify that the permissions allow the expected tasks without exposing unnecessary features.
-
-
Renew and update roles regularly: As your organization grows or new features are introduced, revisit the role configurations to make sure they still align with your security requirements and business needs.
-
Track permission changes: Maintain a log of all changes to role permissions. This can help with audits, troubleshooting, and understanding access history.
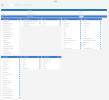
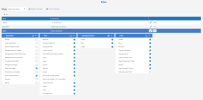
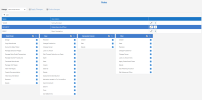
Recommended permissions
The following tables outline the recommended permission values for the default SECURITY and BASIC roles:
General Roles
Data Model Roles
By following these best practices and detailed steps, administrators will establish a robust permissions system that aligns with organizational security policies and enhances the user experience in SEI.
Role assignments and permissions contain sensitive information. Only authorized personnel should view or modify these settings.